Newland NPT is committed to upholding the highest standards of security across our products and services. Our vulnerability management procedure is designed to systematically identify, assess, and mitigate potential vulnerabilities within our products. We encourage responsible disclosure of suspected vulnerabilities by security researchers, industry peers, customers, and partners to ensure timely resolution and ongoing protection of our products and services.
This commitment is reflected in our Security Maintenance Cycle (NSMC), as summarized below. The NSMC is applied annually to all products or triggered immediately upon discovery of critical vulnerabilities, whether through internal vulnerability assessments or external sources like hardware vendors. Task 1 to Task 4 are mandated to be completed within four weeks of detecting vulnerabilities, with Task 5 dependent on Software development (SW) team planning tailored to the criticality of identified vulnerabilities.
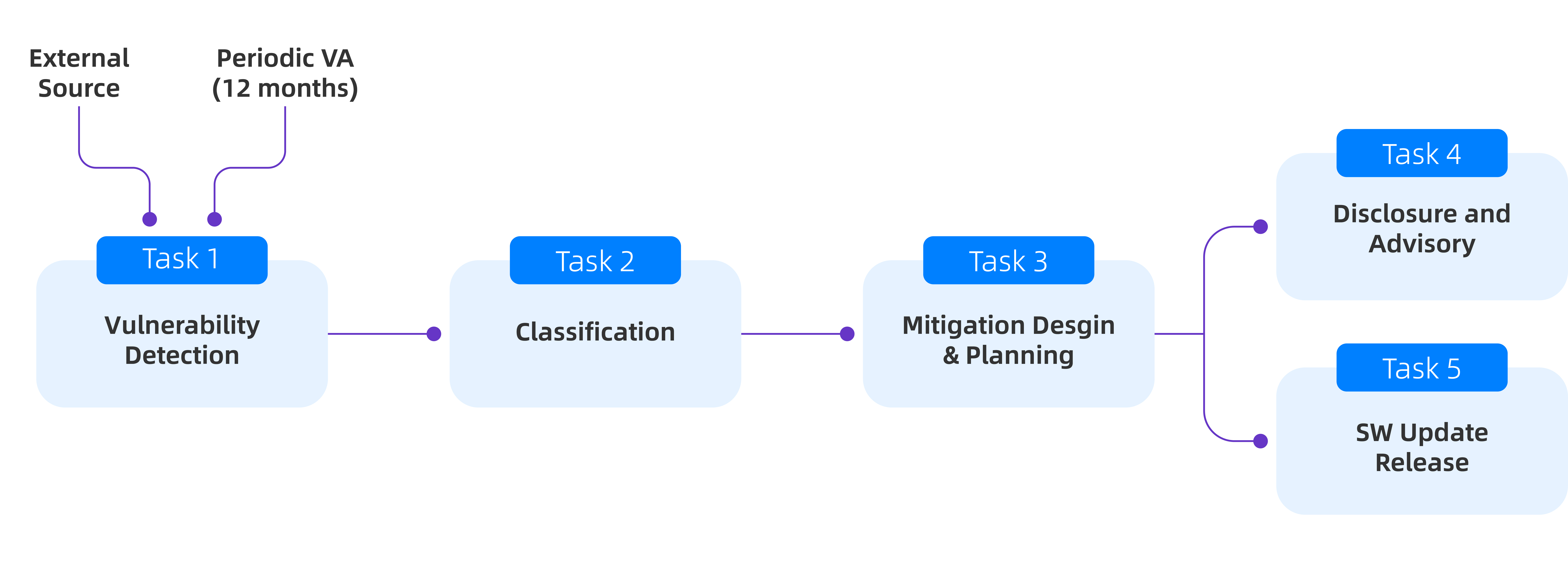
For CRITICAL vulnerabilities, an expedited procedure is implemented where Task 1 to Task 3 are combined, with responsibility shared between the Security and Software Development teams. Task 4 (Disclosure and Advisory) may be postponed for security reasons until Task 5 (Software Update and Release) is complete.
NSMC PROCESS
Task 1: Vulnerability Detection
Expected duration: 7 days
Vulnerability detection channels:
• Regularly check public resources for publicly reported vulnerabilities.
• Proactively liaise with hardware vendors to obtain information about vulnerabilities and mitigation paths.
• Receive private notifications from partners, customers, etc.
Periodic assessments include the execution of the following tasks:
• Vulnerability surveys from all sources1, such as NVD.
• Vulnerability assessment testing2
Note: Users can report vulnerability issues through our email (newland.es@newlandnpt.com). Upon receiving a report, we will acknowledge receipt within 7 days.
Task 2: Classification
Expected duration: 3 days
Newland defines security vulnerabilities according to their criticality and categorizes them into three main levels: low, medium, and critical.
Task 3: Mitigation Design and Planning
Expected duration: 7 days
Develop technical advisory information and plan for software repairs when required. Certain vulnerabilities may be tested to determine their severity.
Task 4: Disclosure and Advisory
Expected duration: 3 days
Dissemination of advisory information to internal and external stakeholders.
Note: When a critical-level vulnerability is discovered, our technical support team will contact the customer within 24 hours. A formal notification will be sent via email, and we will discuss mitigation options with the customer to address the risk.
Task 5: Software Update and Release
Design, implement, and release the fixed software according to the plan defined in Task 3 and the software repair guidelines defined.
CONTACT INFORMATION
Please contact Newland NPT at newland.es@newlandnpt.com for any security-related issues with our products. Please note that only emails sent in English or Chinese can be considered.
We promise to continuously follow up on reported issues and update the status until the reported issues are resolved.
1. For third-party software, at least the manufacturer's website and a third-party vulnerability database will be taken into account.
2. Testing may be conducted internally using the advanced commercial vulnerability assessment tools (e.g. Wireshark, Nessus, NMap…) or with the help of third party service providers. In the case of the service being contracted to a third party, the same level of expertise and tool quality used for internal testing will be defined by contract with the service provider.